



File extension spoofing is a handy trick when creating trojans. In this blog, I will be spoofing the ‘.exe’ extension to the ‘.jpg’ extension. But this method can be extended to spoof any extension type.
I have a file named trojan.exe whose name I will change to sports_complexe.jpg by the end of this blog.



I will use a right-to-left-override character to spoof the extension .exe and replace it with .jpg . Let me tell you how.
Current file name -> trojan.exe
Desired extension -> .jpg
To remove the .exe from extension, I will use a right-to-left-override character to make the file name read from right to left after the right-to-left-override is placed.
Right-to-left of .jpg would be gpj.
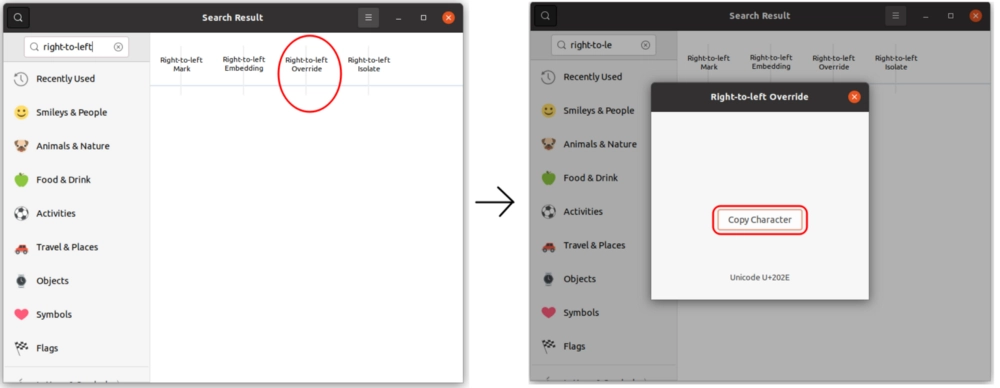
To get the right-to-left-override character open the characters application in Ubuntu and search for the right-to-left-override character. You can follow the steps shown in the pictures below.
Rename trojan.exe to trojangpj.exe . Paste the right-to-left-override character at the 7th position after trojan. All the characters after the right-to-left-override character will be flipped i.e. read right to left.



The filename now looks like trojanexe.jpg
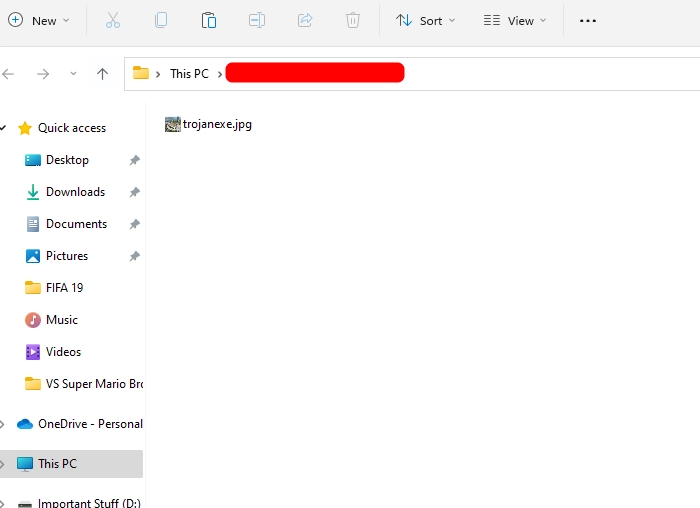

To make the executable look more realistic, since the image icon contained in the file is of a sports complex I will replace trojan in the name with sports_compl so that the file name reads sports_complexe.jpg

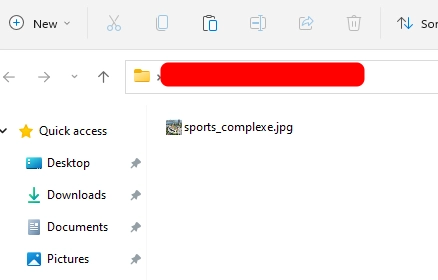

And tada! , the file extension spoofing was successful. Some recent browsers remove the right-to-left-override before downloading. So it is a good idea to zip the file and send it over.
And that’s a wrap! Hi, I am Gourav Dhar, a software developer and I also write blogs on Backend Development and System Design. Subscribe to my Newsletter “The Geeky Minds” and learn something new every week - https://thegeekyminds.com/subscribe
Other Articles
What is an SSL/TLS Certificate and How do they Secure Your Website?
What are WebSockets? Everything you need to know about WebSockets!
How to create the perfect Pull Request?